Understanding Penetration Testing in Software Testing: A Key to Strengthening Cybersecurity
In today's digital age, cybersecurity has become a paramount concern for businesses and individuals alike. As software applications and systems become increasingly interconnected and complex, the risk of cyberattacks has grown exponentially. To safeguard against these threats, organizations must employ robust security measures and one of the most effective tools is penetration testing.
In this blog post, we will explore its significance in software testing, the different types of pen testing, and its role. We will also discuss the challenges associated with pen-testing and common tools used to implement effective pen testing programs.
I. What is Penetration Testing?
Penetration testing, or pen testing for short, is a simulated cyberattack designed to identify and exploit vulnerabilities in a computer system or network. By mimicking the actions of a malicious attacker, pen testing helps organizations assess their security posture and identify potential weaknesses before they can be exploited by real-world threats.
II. Types of Penetration Testing
There are three main types of pentesting: white-box, black-box, and gray-box.
1. White-Box Testing
In white-box testing, the tester has complete knowledge of the system's architecture, code, and configuration. This allows them to focus on specific vulnerabilities and exploit them directly.
Advantages:
- Targeted testing: Testers can focus on specific areas of the system known to be vulnerable.
- Efficient testing: The tester can quickly identify and exploit vulnerabilities due to their in-depth knowledge.
- Comprehensive coverage: White-box testing can uncover vulnerabilities that may be difficult to find using black-box methods.
Disadvantages:
- Limited realism: The tester's knowledge of the system may limit the realism of the attack.
- Internal bias: The tester's familiarity with the system may cause them to overlook certain vulnerabilities.
- Time-consuming: White-box testing can be time-consuming, especially for large or complex systems.
2. Black-Box Testing
In black-box testing, the tester has no prior knowledge of the system's internal workings. They simulate a real-world attack, attempting to exploit vulnerabilities from an external perspective.
Advantages:
- Real-world realism: Black-box testing provides a more realistic assessment of the system's security.
- Unbiased testing: The tester's lack of knowledge prevents internal bias.
- Discoverable vulnerabilities: Black-box testing can uncover vulnerabilities that may be hidden from internal testers.
Disadvantages:
- Inefficient testing: Black-box testing can be time-consuming, especially for large or complex systems.
- Limited coverage: Black-box testing may not uncover all vulnerabilities, especially those that require internal knowledge.
- Risk of false positives: Testers may identify vulnerabilities that are not exploitable.
3. Gray-Box Testing
Gray-box testing combines elements of white-box and black-box testing. The tester has limited knowledge of the system's internal workings, but they may have access to certain internal documents or information.
Advantages:
- Balanced approach: Gray-box testing provides a balance between realism and efficiency.
- Targeted testing: Testers can focus on specific areas of the system based on their limited knowledge.
- Reduced risk of false positives: Gray-box testing can help reduce the risk of identifying vulnerabilities that are not exploitable.
Disadvantages:
- Limited knowledge: The tester's limited knowledge may hinder their ability to identify and exploit certain vulnerabilities.
- Increased complexity: Gray-box testing can be more complex to manage than white-box or black-box testing.
- Difficulty in defining scope: It can be challenging to define the scope of a gray-box test.
III. Penetration Testing Methodology
Penetration Testing Methodology is typically divided into several distinct phases:
1. Reconnaissance Phase (Information Gathering)
This is the first and most crucial phase in penetration testing. The goal is to gather as much information as possible about the target system or network. The more data the tester has, the easier it will be to find potential weaknesses. There are two types of reconnaissance:
- Passive Reconnaissance: Involves collecting information without direct interaction with the target. This includes analyzing public resources such as WHOIS databases, DNS records, social media, company websites, and online forums.
- Active Reconnaissance: This involves direct interaction with the target system, such as pinging the network, port scanning, and footprinting to map the network infrastructure.
2. Scanning Phase
In this phase, the tester actively examines the target system to identify open ports, services running on those ports, and potential entry points. Scanning aims to create a detailed map of the network's vulnerabilities.
- Port Scanning: Determines which ports are open and accessible.
- Network Mapping: Involves detecting live hosts in the network and mapping their IP addresses and services.
- Service Detection: Identifying the version of services or software running on the system to discover known vulnerabilities.
- Vulnerability Scanning: Automated tools are used to scan for known security vulnerabilities in the network and applications.
3. Enumeration Phase
Enumeration builds upon the scanning phase by diving deeper into the details of the system. The goal is to extract more information about the network, hosts, and services.
- User and Group Enumeration: Finding information about users, groups, and roles that exist on the network.
- Service Enumeration: Digging into specific services (e.g., SMB, SNMP, FTP) to discover configuration weaknesses or sensitive information.
- Shared Resources: Identifying shared files or drives that might reveal useful data.
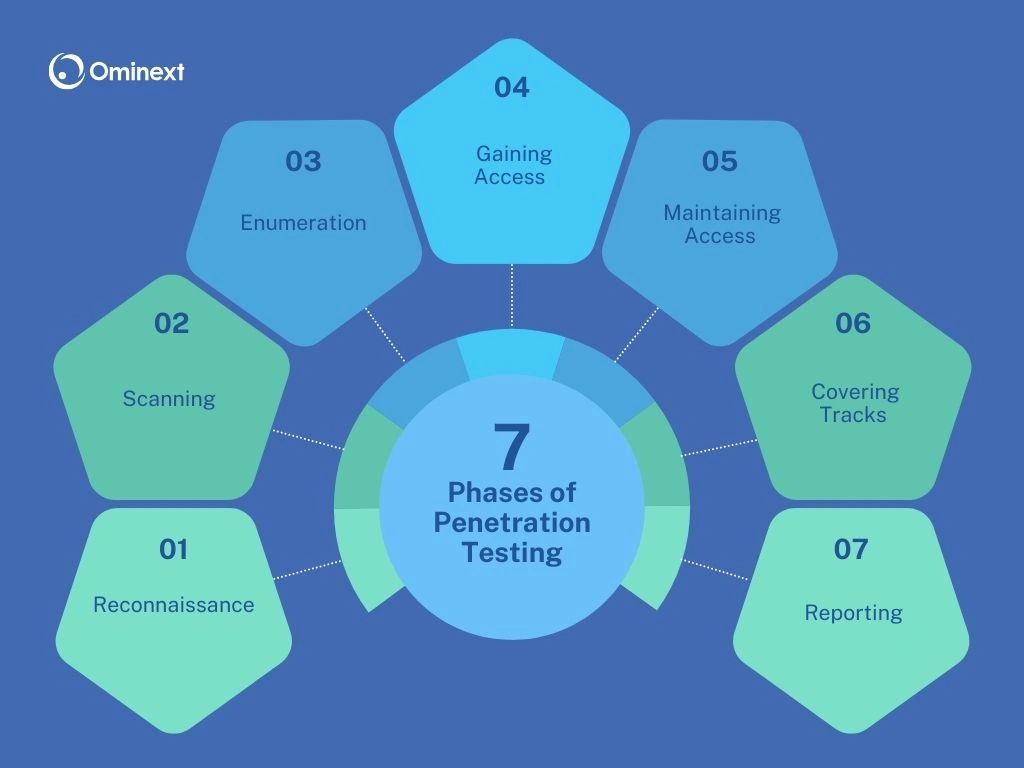
4. Gaining Access Phase
This phase involves exploiting vulnerabilities found in the previous steps to gain unauthorized access to the target system.
- Exploitation: Utilizing tools or scripts to exploit the identified vulnerabilities in the system, whether it's through software bugs, misconfigurations, or weak credentials.
- Privilege Escalation: Once inside, the tester tries to increase their access level to administrative privileges, allowing deeper control and access to sensitive data.
5. Maintaining Access Phase
After gaining access, the penetration tester may attempt to maintain persistent access to the target system without being detected. This ensures they can continue exploring or exploiting the network over a longer period.
- Backdoors: Installing malware, rootkits, or other backdoors to keep access in the future, even if the exploited vulnerability is patched.
- Pivoting: Moving from the compromised system to other systems in the network to escalate the attack and access more sensitive areas.
6. Covering Tracks Phase
In this phase, the penetration tester takes steps to ensure that their presence and actions are not detected. This is crucial in real-world scenarios, as attackers would want to avoid detection to prevent being countered.
- Clearing Logs: Deleting or manipulating log files to remove traces of the attack.
- Obfuscation: Modifying files, timestamps, or system settings to hide any evidence of tampering.
7. Reporting Phase
Once the testing is complete, the results must be documented. The reporting phase involves compiling all findings, including vulnerabilities, successful exploits, and recommended remediation actions.
- Executive Summary: A high-level overview intended for stakeholders and decision-makers.
- Technical Report: A detailed report that includes the vulnerabilities found, methods used, and technical recommendations for fixing the issues.
- Remediation Plan: Steps the organization can take to address the identified vulnerabilities and enhance security.
IV. Common Vulnerabilities Identified Through Penetration Testing
Here are some of the most common vulnerabilities often uncovered through such testing:
1. Injection Attacks
-
SQL Injection: This involves injecting malicious SQL code into a web application to manipulate or access sensitive data.
-
Command Injection: Similar to SQL injection, but this technique is used to execute arbitrary commands on the operating system.
2. Cross-Site Scripting (XSS)
-
Stored XSS: Malicious code is injected into a website's database and later executed when a user visits the affected page.
-
Reflected XSS: Malicious code is reflected back to the user's browser from the server, causing it to be executed.
-
DOM-based XSS: Attacks target the Document Object Model (DOM) of a web page to inject malicious code.
3. Cross-Site Request Forgery (CSRF)
- Attackers trick a logged-in user into performing unintended actions on a trusted site.
4. SQL Injection
- See the explanation under Injection Attacks.
5. Broken Authentication
- Weak or compromised authentication mechanisms, such as default passwords, lack of password complexity requirements, or insecure password storage.
6. Sensitive Data Exposure
- Exposing sensitive information, such as credit card numbers, personally identifiable information (PII), or trade secrets, in plain text or without proper encryption.
7. Missing Function Level Access Control
- Insufficient access controls at the function level, allowing unauthorized users to perform actions they should not have permission for.
8. Security Misconfiguration
- Incorrectly configured systems, applications, or frameworks that can lead to vulnerabilities.
9. Insecure Direct Object References
- Directly referencing objects in URLs or forms, allowing attackers to access unauthorized resources.
10. Insufficient Logging and Monitoring
- Lack of proper logging and monitoring can make it difficult to detect and respond to security incidents.
V. Importance of Penetration Testing in Software Development
Penetration testing (pentesting) plays a crucial role in ensuring the security and reliability of software applications. By simulating real-world attacks, pentesting helps identify vulnerabilities that could be exploited by malicious actors. Here are some key benefits of incorporating pentesting into the software development lifecycle:
1. Proactive Defense Against Cyberattacks
One of the primary benefits of pen testing is the ability to take a proactive stance against cyber threats. By identifying vulnerabilities early in the development process, organizations can address these issues before they are exploited by attackers. This early detection helps mitigate risks, reducing the likelihood of data breaches and other security incidents. By preventing potential attacks, organizations also avoid the financial losses, reputational damage, and legal consequences that often follow successful cyberattacks.
2. Ensuring Compliance with Industry Regulations
Many industries are governed by strict data privacy and security regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Regular pen testing enables organizations to demonstrate compliance with these standards, ensuring that they meet regulatory requirements for protecting sensitive information
3. Improving Overall Software Quality and Robustness
In addition to strengthening security, pen testing also contributes to the overall quality and robustness of software applications. By identifying and addressing security weaknesses, pen testing enhances the software’s reliability. Moreover, fixing vulnerabilities often leads to better performance and stability, which can ultimately improve the user experience. Users are more likely to trust and have confidence in a secure, reliable application, which is essential for the long-term success of any software product.
4. Gaining Insights into Real-world Attack Vectors
Pen testing provides invaluable insights into the types of attacks that could target software applications. Understanding these real-world threats enables organizations to make informed decisions about their security measures and how to allocate resources effectively. With this knowledge, organizations can develop more robust security strategies that are tailored to defend against current and emerging threats. This enhanced defensive posture ensures that software remains resilient in an ever-evolving threat landscape.
VI. Common Tools Used in Penetration Testing
Penetration testing relies on a variety of tools to efficiently and effectively identify and exploit vulnerabilities. These tools can be categorized into automated tools and manual testing techniques.
Automated Tools
Automated tools streamline the pen testing process and enhance efficiency. Here are some commonly used examples:
- Nmap (Network Mapper): A powerful network scanning tool used to discover hosts, services, and vulnerabilities on a network.
- Metasploit Framework: A comprehensive platform for developing, testing, and executing exploits against vulnerabilities.
- Burp Suite: A web application security testing tool that includes features such as proxy, scanner, intruder, repeater, and sequencer.
- OWASP ZAP (Zed Attack Proxy): An open-source web application security scanner that provides automated vulnerability scanning and manual testing capabilities.
Manual Testing Techniques
While automated tools are invaluable, manual testing techniques are often necessary for deeper vulnerability analysis and to identify issues that may be missed by automated tools. Manual testing techniques include:
- Manual code review: Examining the source code of applications for vulnerabilities.
- Fuzzing: Providing invalid or unexpected inputs to applications to identify vulnerabilities.
- Social engineering: Simulating social engineering attacks to assess the vulnerability of people and processes.
- Protocol analysis: Analyzing network traffic to identify vulnerabilities and potential attacks.
In practice, a combination of automated and manual tools is often used to achieve the best results. Automated tools can quickly scan for vulnerabilities and provide a baseline assessment, while manual testing can focus on specific areas of interest and identify more complex issues.
By effectively utilizing both automated and manual techniques, penetration testers can provide comprehensive and valuable insights into a system's security posture.
VII. Challenges of Penetration Testing
Penetration testing also faces specific obstacles related to:
Balancing Testing with Business Operations
- Avoiding Disruption: Pentesting can sometimes disrupt normal business operations, especially if it involves testing critical systems. Balancing the need for testing with the need to maintain business continuity can be a challenge.
- Minimizing Downtime: Techniques such as non-disruptive testing, scheduled testing windows, and careful coordination with business teams can help minimize downtime.
The Complexity of Testing in Large, Dynamic Systems
- System Heterogeneity: Large, complex systems often involve a variety of technologies, platforms, and configurations, making it challenging to test all potential vulnerabilities.
- Interdependencies: Identifying vulnerabilities in a complex system can be difficult due to the interdependencies between different components.
- Dynamic Environments: Systems that are constantly changing or evolving can make it challenging to maintain a comprehensive testing program.
Evolving Nature of Cyber Threats
- Emerging Threats: New vulnerabilities and attack techniques are constantly emerging, requiring penetration testers to stay updated on the latest threats and trends.
- Adapting Methodologies: Pentesting methodologies must evolve to address new threats and techniques. This may involve using new tools, developing new testing approaches, or modifying existing procedures.
Skilled Personnel Required for Effective Testing
- Specialized Knowledge: Effective penetration testing requires a high level of technical expertise and a deep understanding of security principles.
- Ethical Considerations: Penetration testers must also be aware of ethical guidelines and legal requirements to ensure that their activities are conducted responsibly.
- Skill Shortage: Finding qualified penetration testers with the necessary skills and experience can be challenging, especially in certain regions.
Conclusion
Penetration testing is an indispensable tool for strengthening cybersecurity in today's digital landscape. By simulating real-world attacks, pen testing helps organizations identify and address vulnerabilities before they can be exploited by malicious actors.
As technology continues to evolve and new threats emerge, the importance of penetration testing will only grow. By incorporating pen testing into their software testing processes, organizations can proactively protect their systems, data, and reputation.
In summary, understanding penetration testing and leveraging its benefits is crucial for building a strong and resilient cybersecurity posture.





